OPS345
DNS and SSL Certificates
Eric Brauer
What Is DNS?
Machines use IP addresses:
10.3.45.109
Humans prefer URLs:
https://learn.senecacollege.ca
DNS turns one into the other.
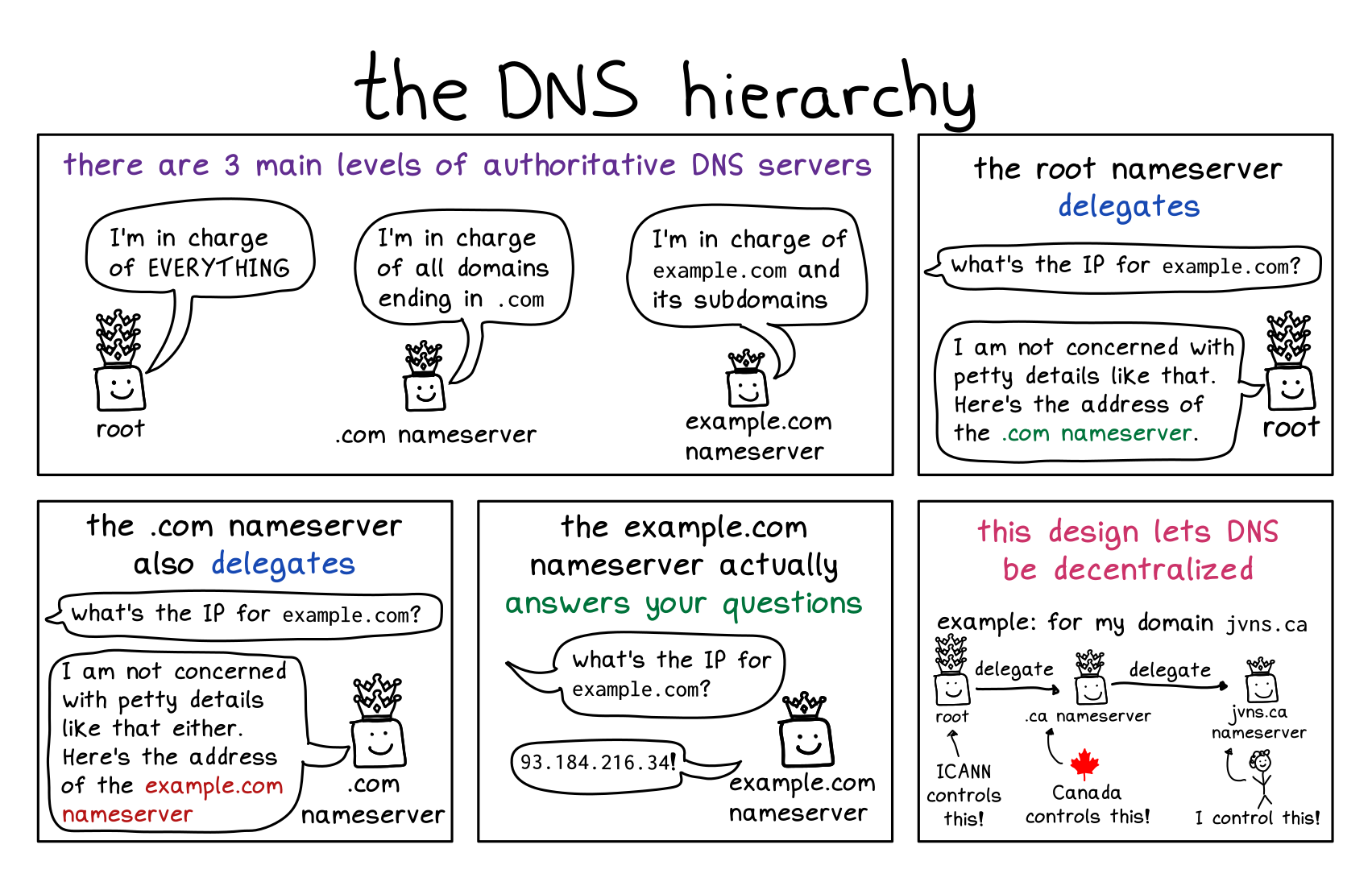
Introduction to DNS
Of course, with most things networking, the implementation is much more complex than the concept.
DNS isn’t just looking things up in a phone book… it is more decentralized than that.
Introduction to DNS
BTW, I bought this zine, and you can support the artist
In A Nutshell, What Does It Mean For A Lowly SysAdmin?
- If you want to associate an IP address to a URL, it usually costs $$.
- We can choose to set up a private DNS server for internal use, meaning we can associate private IP addresses with URLs.
For this course, you will use the Bindistrar credentials I emailed you earlier in the semester.
CLI Tools
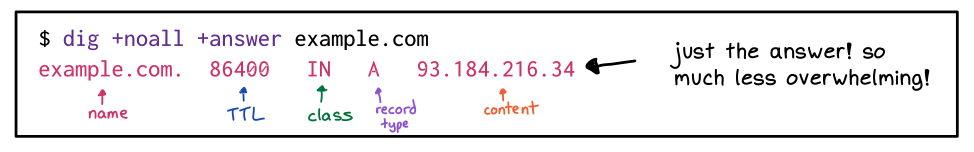
There are several tools demonstrated in the lab, but let’s focus on
dig.
The full output can tell you if there was an error, but you can also simplify the response:
DNS Records
A:: translates URL to IPv4.
AAAA:: translates URL to IPv6.
CNAME:: translates URL to another domain name.
In other words, redirects a URL request to another URL.
Fixing Nextcloud
- Read the error message carefully.
- Read the error message carefully always!!
- There is a php file, so do you open it from the browser?
- No, use vim.
- Omit the ‘www’ from the beginning of the domain (or don’t, you’ll see the difference at the end).
What Is Encryption?
A: Take data, convert it into junk that can’t be understood. In a way that can be converted back into data, but only by certain people you trust!
abc 👉 xnc
The pointing hand implies a key, some algorithm that can convert sense into nonsense, and back again, in a way that can’t be understood by an outside observer.
Symmetric Encryption
An example would be a Caesar Cypher, basically the algorithm is ‘every character gets turned into the next letter’.
cat 👉 ‘dbu’
- the key to decrypt is just the inverse of the key to encrypt.
- this code is cracked by third-graders for fun. So it’s not secure.
Asymmetric Encryption
- Instead of one key, there are two.
- One key encrypts, to other decrypts.
- This makes more interesting things possible!
Encrypting With A Public Key
- One key becomes my public key. I give this to Bob.
- One key becomes my private key. I keep this one safe.
- Anyone can lock messages, but I’m the only one who can unlock it.
Therefore: people can be confident only I am able to read the message.
Encrypting With A Public Key
graph LR;
UM[Bob's Computer]
PUK{Eric's Public Key}
EM[The Internet]
PRK{Eric's Private Key}
UNM[Eric's Computer]
UM-- "Dear Eric..." -->PUK;
PUK-- "xrrgsdlkjdfj" -->EM;
EM-- "xrrgsdlkjdfj" -->PRK;
PRK-- "Dear Eric..." -->UNM;
Encrypting With A Private Key
- If Bob uses his private key to lock a message, anyone can unlock and read it (as long as they have his public key).
- However, if I can unlock his message using his public key, that means it could have only been created with Bob’s private key.
Therefore: I can be confident that this message actually came from Bob and nobody else.
Encrypting With A Private Key
graph LR;
UM[Bob's Computer]
PUK{Bob's Private Key}
EM[The Internet]
PRK{Bob's Public Key}
UNM[Eric's Computer]
UM-- "Dear Eric..." -->PUK;
PUK-- "xrrgsdlkjdfj" -->EM;
EM-- "xrrgsdlkjdfj" -->PRK;
PRK-- "Dear Eric..." -->UNM;
Putting It Together
- Bob writes a message, and locks it with both Bob’s Private Key and Eric’s Public Key.
- Only Eric can read it, only Bob could have sent it.
- Eric does the same
- We have established secure two-way communication
Even More
Wow, the way I’m going on about this, seems like it might be important…
Asymmetric Encryption Using SSH
- If you encrypt using your private key, and I have your public key, then I can verify your identity.
- If I encrypt using my private key and your public key, then we can be sure that your traffic is safe.
- But what if I can’t be sure I have your actual public key?
- When we establish an SSH connection, you may get a Man In The Middle Warning.
Applying Encryption To The Internet (HTTPS)
- What about when we visit a website? We can’t revert to passwords if we’ve never visited before.
- We need a third party that can vouch for a particular website and certify its public key.
- We call these Certificate Authorities (CA)s.
Selecting A Certificate Authority (CA)
- Most require $$$, but Let’s Encrypt does not.
- You can generate a cert using a command line utility
- Package is called
certbot, and it should be available in Linux Mint repos. - You could install
certboton one of your instances (I did), but it takes extra steps and I don’t recommend it.
Running Certbot
- In the instructions, you’ll notice some
digcommands partway through the process. - I recommend you finish the process before running
dig(especially if you’re generating certs on an instance).
HTTP vs. HTTPS
Once you have completed Apache configuration changes, you’re not done!
- Recall that HTTP uses port 80, but HTTPS uses port 443.
- That’s right, you’re modifying
iptablesand security groups again